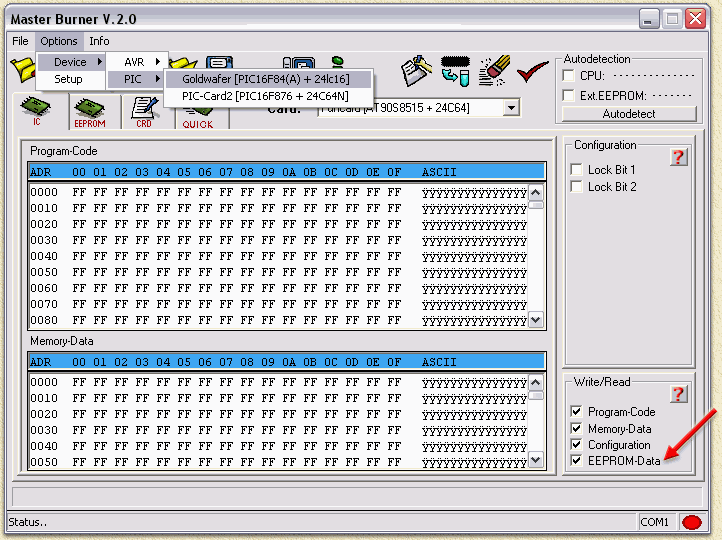
Software Conax Decrypter
MEO File Encryption Software Encrypt and decrypt files and keep your data secure. MEO is easy file encryption software for Mac or Windows that will encrypt or decrypt files of any type. Protect sensitive data against unauthorized viewers with the latest data encryption technologies to keep your important documents safe and secure. What third party software is used? Is there an overview of all options available? Conax Contego provides Conax' own variant of HLS PlayReady encryption. Please see Conax PlayReady for the outline of its use. Consult the Conax Contego manual on how to obtain the required variables from the Conax Contego API. Batman arkham city pc mod.
Some of the ransomware decryption tools mentioned below are easy to use, while others require a bit more tech knowledge to decipher. How to avoid ransomware in the futureOne of the most efficient ways to prevent the threat of ransomware from wreaking havoc and locking your sensitive data is to remain vigilant and be proactive.In fact, we strongly recommend you to apply these basic and simple steps we outlined in the, that can help you prevent this type of cyber attack.Even if cyber criminals get access to your computers and infect them with malware, you can just wipe the system clean. No money lost and, most importantly, no important information compromised!
So, please, do not postpone the process of doind a backup of your data. Not tomorrow, not this weekend, not next week. Do it NOW!Also, it helps raising awareness on this topic and share the basics of with your friends and family, because it could prevent them from being a ransomware victim.As new types of emerge, researchers decrypt some strains, but others get new variants, and it may look like a cat and mouse game, in which proactivity is vital. Quick checklist for ransomware protectionFollowing this actionable protection guide will help both Internet users and organizations to better prevent ransomware attacks causing so much damage. Take the time to read this actionable checklist in which you can learn more about enhancing your online protection.This article was originally published by Andra Zaharia on October 5th, 2016 and was updated by Ioana Rijnetu in March 2019. Rajarathinam SelvarajYour files are now encrypted!All your files have been encrypted due to a security problem with your PC.Now you should send us email with your personal ID.This email will be as confirmation you are ready to pay for decryption key.You have to pay for decryption in Bitcoins. Phil BostonHi,I have been wiped out by ransomware, files have the extension.ltxqy added to file names.Does anyone have any info on this please as I cannot find any reference, the ransom text reads:Do not rename the ciphered filesDo not try to decrypt your data of the third-party software, it can cause constant data lossYou do not joke with filesTo restore your files visit “website.
This website is safeIf this website is not available use reserve website “in a TOR network. This website is safe. For visit of this website it is necessary to install Tor browser Your login: CjeD3IuOayEmtkvYour password: iVTMsu59woh4NkcYour BTC address: 1DMtUCEkD7zfJrdn7b33cApZpTdmKiRd5EIf all websites are not available write to us on email ofYou keep this information in secret.
JThanks Ioana, we’re horrified that it managed to punch through both our filtering system and McAfee VSE antivirus without either of them picking it up. Thankfully we were able to triage the system that had been originally hacked (was running a bluestacks VM which was pushing out all sorts of nasties back to our file servers after hacking our local system administrator password and a low-access domain user password), isolate the affected areas, delete the encrypted data completely and recover those files from backups so ultimately we lost a day’s worth of files at most in non-critical areas of the network. No sign that there was any attempt to steal the data, simply lock it up, so as far as these things go I feel we got off fairly lucky. I will definitely upload one of the affected files to that tool and see if it can identify what hit us, thanks for the response 🙂.
HerculespuaroMy server have been infected by trojan recently and all files got encrypted. Now they all have ‘.combo’ extension =Filename.ppsx.id-6E93B7E4.bhurda@aol.com.combo=. After long search, I found out, that there is no decryptor for it. With no other choice I wrote to email, and since data on server was important, decided to pay.
Download free applied linear algebra olver shakiban pdf converter. We will be surveying calculus on. Is a linear combination of the basis vectors. 10 Olver, P.J., and Shakiban, C., Applied Linear Algebra, Prentice–Hall, Inc., Upper. These solutions need not be written in pen. Download our applied linear algebra olver and shakiban eBooks for free and learn more about applied linear algebra olver and shakiban. Applied Linear Algebra by Peter J. Olver and Chehrzad Shakiban Corrections to Student Solution Manual Last updated: July 21, 2013 1.2.4(d) A = 2 −1 2 −1 −1 3 3 0 −2, x =.
We dealed on 0.8 btc, and I paid on my own risk. Guys have send me the decryptor right after transaction approved, and they’ve seen it. If your data is important I advice you to pay. Do not use other decryptors – they’ve destroyed my test files. AmarI am also a suffered person by ransome in 2017, it was my first time experience, before that I never had heard about it, after having a massage in my desktop screen I immediately format my system and that was a big mistake ever I done. My 10 years working effort spoiled for some creepy minded people. Till now I am in hope that one day I able to recover my all valuable data.
Want your help to recover my file if there was any possibilities after format. The code which they have send is SPEy0oxc1mpzzb0cY-1BA4C2C55A5602F0. M.Cihan ErdemAs known recently New Dharma Ransomware is under fast distribution and all important documents like (sql,mdf,log,pdf,doc,docx, xls,xlsx,dwg,mp3,mp4,mpeg,avi,jpg, bmp,vb) are encrypted with extensions (arrow, java, cesar, arena, bip or combo) and not usable/readable unfortunately. If you and one of your customers/friends are infected of this ransomware you could send 3-4 encrypted files (XLS, DOC, PDF or Photo File) to below email address, After checked your files, you will be informed within 1-2 days.Email. KeZaJust use Qubes OS and ditch windows and live your life. Problem solved!
If I need to believe you al than here on Xp I have and entire store of ransom, malware, ect. You all need to stop with this because this is not fun anymore. You need to now your pc in and out and fir the best is Windows 7 if you stay on Windows. Windows 10 is crapware and will die out and just follow the reactions on Ghakcs when there is a article of W10. These people are an example that know more then the laypeople and the most of them discard W10 because it’s crapware. DaniloHello Andra,I have many jpgs and video files which I backed up from a memory card I used on a Blackberry long time ago.This device was stolen, and most part of the files are on the.rem RIM’s extension.My question is: is told that just the original device which encrypted the original file can open and decrypt it; files saved/backed up from the original memory cards cannot be read on Macs/PCs.Is there any software that could do this job in my case, as I had it stolen a long time ago on the airport?Best. Andra ZahariaCyber security experts, the Europol, the FBI and many more authorities and specialists advise to never pay up.
There is no guarantee that you’ll get your data back or that the decryption key will work. There are cases where the ransomware is poorly coded and can’t be decrypted, even with the correct key, because the encryption went badly. Also, paying the ransom will just feed the malware economy and enable cybercriminals to continue attacking people and companies all over the world.
Your name will appear next to your review or comment, visible to everyone. We (Satworld) also save your IP address as a security precaution, but in can only be viewed by our staff. It will remain in our system until you withdraw your consent. If you’d like to have your personal data removed, send an email toIf you believe that your personal data has been misused, you have the right to lodge a complaint with a supervisory authority.
We’re obliged by EU General Data Protection Regulation to let you know about this right; we don’t actually intend to misuse your data.